Summary:
Recently I got 4 CVEs for reporting security issues in an opensource software namely SeedDMS. This particular post talks about the Exploit for CVE-2019-12932 which was present in SeedDMS 5.1.11 and has been patched and 5.1.12 has been released to fix the same.
Exploit:
- Login to the application as a user and make a new folder, with your payload in name parameter as shown.

- Now save it as shown.

- Now search for the folder name to execute the XSS.
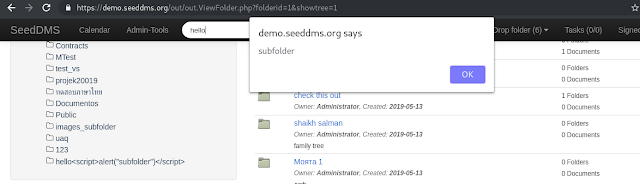
I try to keep my posts as precise and to the point so incase you face any issue replicating the same, feel free to comment.
Comments
Post a Comment